© ROOT-NATION.com - Use of content is permitted with a backlink.
Motorola means different things to different folks, but to us, it’s always been a company that tirelessly innovates and brings us some of the most exciting new devices. Still, foldable phones and new displays are cool at all, but they might not be the most important piece of new technology Motorola has given us. That title goes to ThinkShield. But what is it exactly — and why should you care?

Unexciting but necessary
Security is boring — we get it. Nobody thinks about it as long as it works, but when something goes wrong, all hell breaks loose. In a survey conducted in 2020, findings revealed that 46% of organizations disclosed incidents where an employee unwittingly downloaded a malicious mobile app. Furthermore, a staggering 97% of organizations encountered mobile threats employing diverse attack vectors throughout the year, heightening their susceptibility to escalating data and security risks. In short, it’s a big problem.
ThinkShield is a robust security suite designed for enterprises, a formidable defense against the ever-present threats of data breaches and cyberattacks.
At its core, ThinkShield encrypts sensitive data, fortifying it against unauthorized access and potential leaks—a pivotal shield for companies safeguarding their valuable information.
Read also: To out-innovate your rivals. How Motorola keeps us entertained
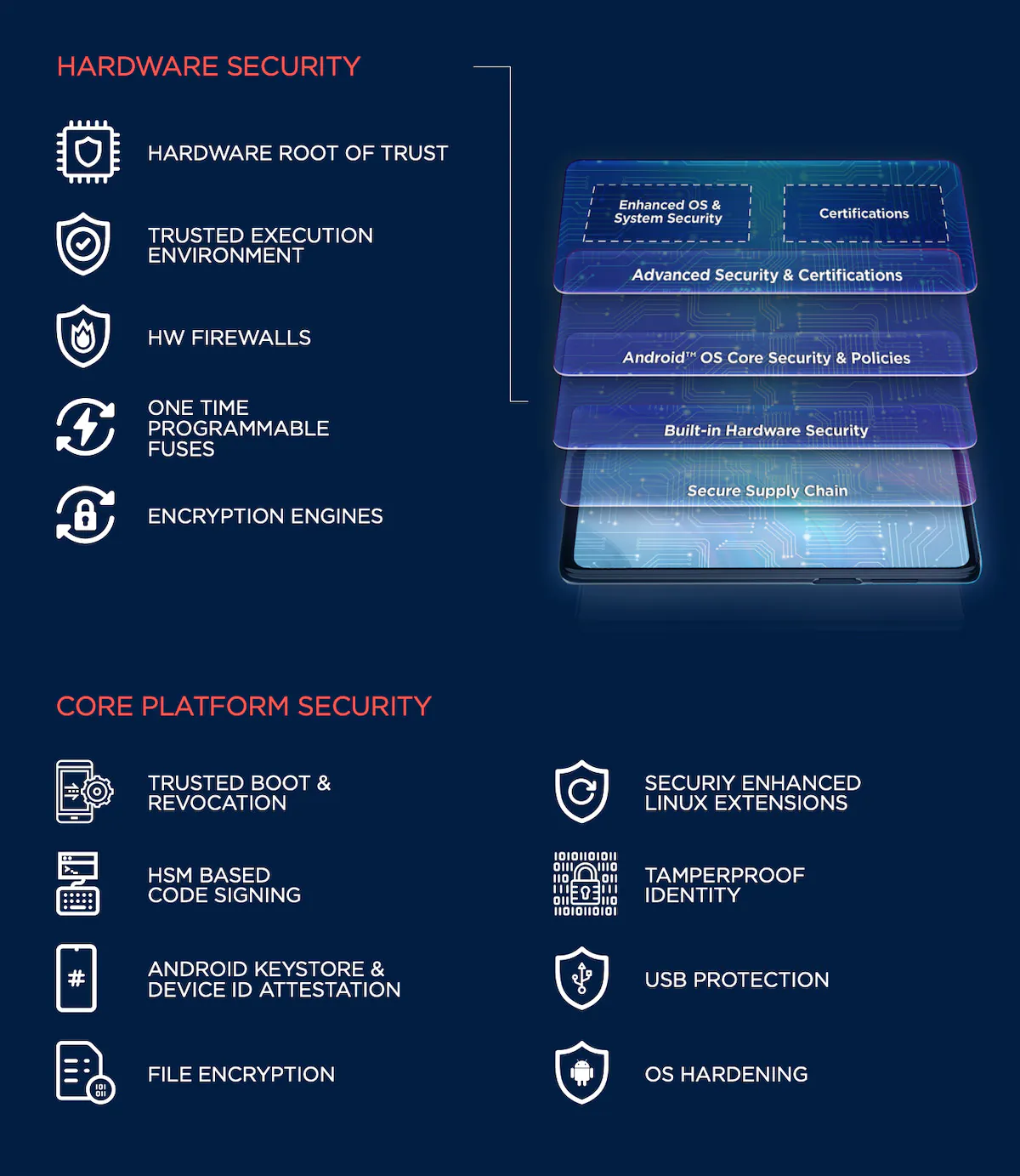
The operating system undergoes heightened security measures. Actions such as random bootloaders and development activities that could compromise security are unequivocally off-limits, contributing to a more resilient defense.
Delving into the digital realm, the browser, its associated sandbox, and cache are not just features but safeguards, providing an additional layer of protection against potential vulnerabilities.
Moving beyond the virtual landscape, the hardware aspect of ThinkShield is equally impressive. From WiFi to radio bands and even the 3.5mm jacks, USB ports, and various I/O connections—all are fortified with business-grade security.
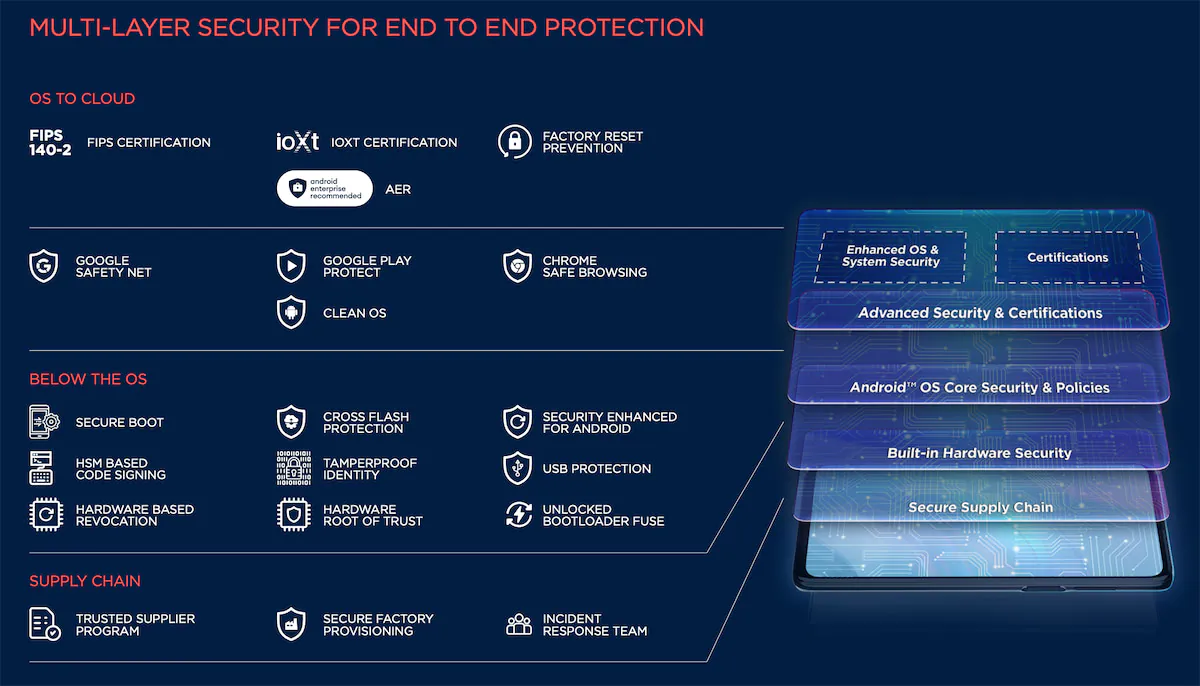
Motorola takes a dynamic three-pronged approach to keep your device safe
At its heart, ThinkShield for mobile is like armor, incorporating crucial security elements in a protective shield to wrap your entire device, including the operating system.
The supply chain, hailed by Gartner, is the unsung hero, undergoing intense evaluations to ensure that component suppliers are as security-savvy.
Digging deeper, the Below the OS Security is like the device’s personal bouncer, implementing stuff like trusted boot and revocation, ensuring it’s a fortress inside out.
And when it comes to the OS to Cloud Security, think of it as the device’s travel companion, making sure it’s not just stylish but secure, with a clean OS and advanced features, navigating the cloud with ease.
This system of systems makes Motorola phones one of the most protected on the market. It’s hard to make it sound exciting but even harder to underestimate its importance.
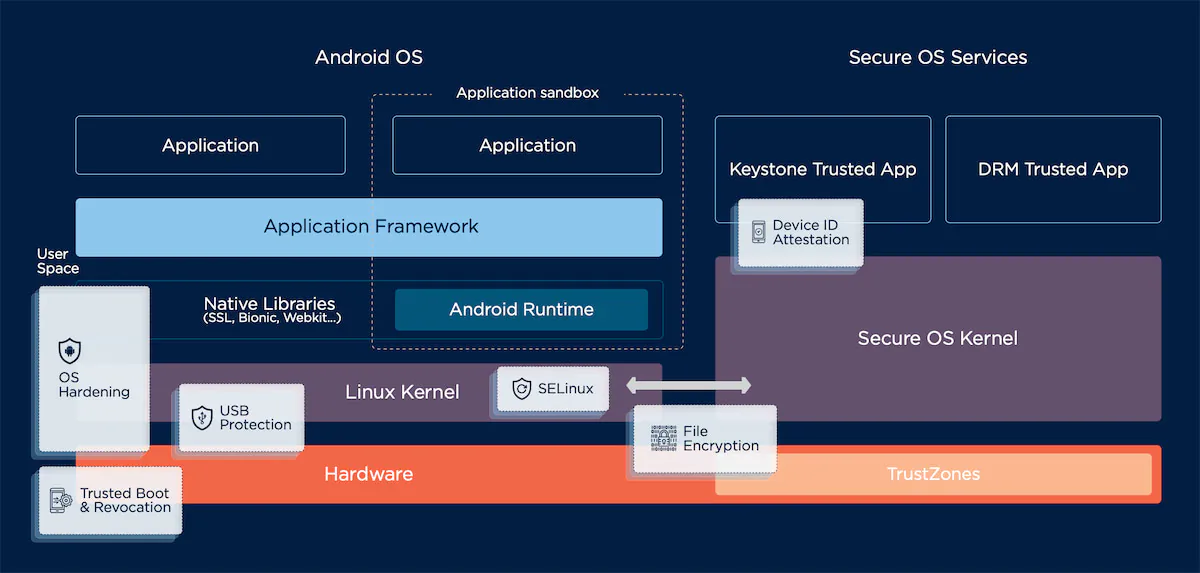
When it comes to keeping your mobile device secure, ThinkShield goes the extra mile with a special feature called a hardware-backed keystore. This keystore is like a super-secure vault that operates separately from the regular Android system.
What does it do? Well, it’s all about ensuring that the security keys are safe. These keys are tied specifically to your device or a particular app and protected from theft. The keystore achieves this by using some advanced hardware inside your device and a special encryption key.
Here’s the cool part: even if an attacker manages to exploit a vulnerability in an app that holds these keys, they can’t actually take the keys out. And, even after fixing the vulnerability, the keys stay safe.
How does it work day-to-day? The keystore gets its instructions from the Trusted Boot process and authentication modules like fingerprint recognition. During the early boot-up of your device, the Trusted Boot process gives important details to the keystore, such as the security status, software version, and anti-rollback info. If there’s anything suspicious, like an old software version or the device not being secure, the keystore stops access to the keys. Also, the keys can be set up to need authentication before they can be used, adding an extra layer of security.
Now, there’s another cool feature called Device ID Attestation. This means your device can prove its identity by sharing details like its name, model, manufacturer, and serial numbers with another party. This is especially handy for business scenarios like zero-touch setups. To make this feature super secure, the hardware details are locked into the device during manufacturing, ensuring they can’t be tampered with.
Read also: Motorola celebrates 10th anniversary of Moto G series with 200 million devices sold
Lost your phone? No need to worry
Your lost or stolen device is like a ticking time bomb, vulnerable to physical attacks that could spill all your personal information. Thankfully, Motorola has a (yet another) nifty trick up its sleeve.
By default, your phone blocks any new USB connections when your device has a secure lock screen. That includes the Android Debug Bridge (ADB), the tool that tech-savvy users might use for some heavy lifting.
Why does this matter? Well, imagine a scenario where an attacker tries to exploit your device through the USB port. Motorola’s move is like slamming the door shut on any sneaky attempts to mess with the USB protocol stack or services that use USB.
So, even if your device falls into the wrong hands, this USB lockdown is an extra layer of defense.
Motorola’s Product Security Incident Response Team (PSIRT)
Now to something that actually does sound kinda cool. Maintaining a secure product lifecycle is crucial in the ever-changing landscape of evolving threats. Vigilantly monitoring, analyzing, and swiftly patching security vulnerabilities before they become exploitable is a vital part of this process. Motorola’s Product Security Incident Response Team (PSIRT) takes an active role, managing reports from various sources, including vendors, customers, and researchers. They also closely monitor the internet and dark web for potential threats that could impact their devices.
That team is committed to a rapid response, ensuring that all reported product vulnerabilities are acknowledged within 48 business hours. Every discovered vulnerability is meticulously documented in the tracking system. They thoroughly analyze factors such as product applicability, severity, and the most effective patching strategy. This involves seamless coordination with vendors and internal teams to deliver the necessary patches.
What is OS Hardening?
Motorola’s got your back when it comes to Android security. They don’t just stop at the surface – they dive deep into the nuts and bolts of things.
First off, let’s talk about the board support package. Moto weeds out any unnecessary features that might be lurking around, ready to cause trouble. Then there are the preloaded apps – we all know those can be trouble. The security squad goes through each one with a fine-tooth comb. They check if any of them are asking for too much permission, if they’re playing nice with APIs, and if they’re using secure connections (HTTPS). The goal? Ensure your phone doesn’t get into shady dealings with these preloaded apps.

Motorola doesn’t just rely on their in-house security pros. They bring in third-party consultants to do a deep dive into the system. These external experts turn over every virtual stone, ensuring no hidden vulnerabilities are waiting to ruin the party.
And for some devices, they even take it a step further by joining Google’s Advanced Assurance Program. It’s like the VIP section of security audits. These devices go through the wringer, meeting and often exceeding all the security requirements set by the big G.
How does ThinkShield compare to Samsung Knox?
In contrast to Knox, which boasts a comprehensive defense mechanism with its additional layer of physical hardware-based protection, ThinkShield primarily relies on software and firmware safeguards.
While both ThinkShield and Knox prove to be highly competent in the realm of device security, the distinction lies in Knox’s unique approach. Knox incorporates a failsafe at the hardware level. Once the integrity of the device’s security is compromised, a hardware fuse breaks, leading to a decisive outcome—the phone either bricks itself or strategically limits functionality to staunchly protect user data.
Final thoughts
We are used to not thinking about cybersecurity — not because there are no threats, but because the devices have become so good at neutralizing them out of the box. And Motorola is, without a doubt, one of the best at it.

