© ROOT-NATION.com - Use of content is permitted with a backlink.
Many people have heard about end-to-end encryption, but not everyone understands how it works. Today, we’ll take a closer look and try to break it down.
In an era where digital communication has become ubiquitous, the importance of securing these interactions cannot be overstated. End-to-end encryption (E2EE) is a key technology in this field, ensuring that data remains confidential and secure from its source to its destination. E2EE is a secure method of communication that prevents any third party from accessing data while it is being transmitted between two endpoints.

The concept of E2EE is not just a modern technology; it has roots in the field of cryptography, evolving alongside advancements in digital technologies. Its origins trace back to the 1990s when Phil Zimmermann introduced Pretty Good Privacy (better known as PGP). Initially developed as a security tool for military and diplomatic communications, E2EE has now become an essential part of securing everyday online interactions.
Read also: 10 Examples of the Strangest Uses of AI
Encryption methods
Encryption is the practice of disguising information in such a way that it remains unreadable to unauthorized third parties. This obfuscation is achieved by using mathematical functions to transform plain data into a code, which can only be deciphered through a specific reverse process, often involving a “key” to facilitate decryption as a form of authentication.

However, there is no universal approach to encrypting all data. Instead, encryption is applied in various ways depending on the specific use case of the data. Let’s take a closer look at each of these methods individually.
Read also: Europa Clipper: Everything You Need to Know Before the Launch of the Largest Spacecraft
Encryption in the rest state
Many computer operating systems, such as macOS and Windows, offer “full disk encryption.” This means that files are encrypted on the disk when they are not in use. Essentially, encryption is applied to protect data at rest—when it is stored or not being actively used. The encryption of this data is carried out using a cryptographic key or hashing algorithms.
It’s worth noting that this method is less vulnerable to breaches, as attackers would need to decrypt the data to make use of it. This method is often employed in combination with other security measures, such as authentication, access control, and data loss prevention.
Encryption during transfer
Encryption in transit is a type of cryptographic protection that prevents data leaks while data is being transferred between two systems or networks over a public or shared network, such as the Internet. When data is encrypted during transmission, it is safeguarded from eavesdropping, tampering, and other malicious activities. Encrypted data is less vulnerable to spying and similar threats, making it safer for use in public or shared networks.
Encryption prevents the interception of messages during transmission but creates a potential vulnerability during decryption. The Transport Layer Security (TLS) protocol is an example of encryption in transit.
Read also: Top 5 Powerful Gaming Smartphones of 2024
End-to-end encryption
Data using this method is encrypted during transmission from the device to the server. Furthermore, the data remains encrypted until it reaches the recipient’s device. This protects against not only attackers who are monitoring the data flow over the Internet but also those who might gain access to the server.
What makes end-to-end encryption unique compared to other encryption systems is that only the endpoints—the sender and the recipient—are capable of decrypting and reading the messages.
Today, we will delve into the intricacies of end-to-end encryption, exploring its real-world applications, advantages, and limitations, as well as its use cases and implementation challenges. We will also examine compliance requirements, potential threats and attack scenarios, and the inherent risks associated with end-to-end encryption.
Read also: IPS vs VA Panels in Monitors: Which One to Choose
What is end-to-end encryption?
End-to-end encryption (E2EE) is a secure method of transmitting data from a user’s device to the recipient’s device, concealing the information from any intermediaries, such as email service providers. With E2EE, data is encrypted on the sender’s device and decrypted only on the recipient’s device. The data never resides in the cloud, as only the sender and the recipient possess the keys for encrypting and decrypting the message. As a result, attackers monitoring internet traffic or breaching a server cannot access the data. This ensures that the information cannot be read or altered by any intermediaries, including internet service providers, hackers, or even communication platform providers.

Many popular messaging service providers, including Facebook, WhatsApp, Telegram, Skype, and Zoom, utilize end-to-end encryption. This technology makes it difficult for providers to share user information from their services with authorities, which could potentially facilitate private messaging for individuals involved in illegal activities. As a result, debates often arise regarding the decision to implement E2EE.
End-to-end encryption is a powerful tool in the arsenal of digital security, playing a key role in protecting the privacy and integrity of online communications. Understanding how E2EE works and how this method differs from other encryption techniques is essential for assessing its importance in today’s digital landscape.
Read also: Why memory is soldered in laptops: advantages and disadvantages
How does end-to-end encryption work?
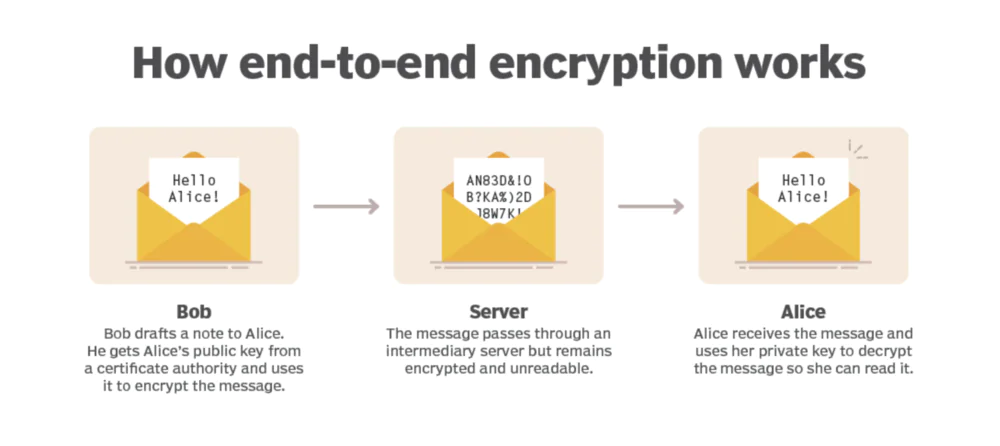
E2EE employs cryptographic keys for encryption and decryption. Each party in the communication has a pair of cryptographic keys—one public and one private.
In other words, end-to-end encryption primarily relies on asymmetric encryption, also known as public key cryptography, to secure data during transmission. Asymmetric encryption involves the following steps:
- The sender and recipient generate a pair of cryptographic keys: a public key and a private key.
- The public key is shared openly, while the private key is kept secret.
- The sender encrypts the message using the recipient’s public key, making it accessible only to the recipient, who possesses the corresponding private key.
To ensure that encrypted data remains secure, encryption methods rely on complex transformations that make it virtually impossible to reverse these transformations without proper access.
In other words, E2EE functions by encrypting data in such a way that only someone with the correct secret number (key) can decrypt it. With end-to-end encryption, the encryption and decryption process utilizes a unique pair of keys for securing and accessing the message. One of the keys in the pair is used solely for encryption, while the other is designated for decryption.
Read also: How to Disable the Firewall in Windows 11
Examples of end-to-end encryption
End-to-end encryption is implemented in various communication tools and data storage services to safeguard users’ privacy and security. This includes messaging apps like WhatsApp, Messenger, Discord, Signal, and Telegram, which encrypt text messages and media files exchanged by users. Email services like ProtonMail and Tutanota also use E2EE to protect users’ emails from unauthorized access. Additionally, E2EE is utilized in file storage and transfer services such as Tresorit and SpiderOak, ensuring a secure method for storing, syncing, and sharing files.

It’s also important to mention online banking and payment apps. Many financial institutions and payment systems use end-to-end encryption to secure transactions and protect sensitive financial data from potential eavesdropping or fraud.
Moreover, E2EE is increasingly being used in Internet of Things (IoT) devices, especially in smart home ecosystems, to secure communication between devices and safeguard user data from unauthorized access.
These examples highlight the widespread use and importance of this encryption method in protecting digital communications across various platforms and services. By encrypting data directly between users, E2EE provides a high level of security and privacy, which is crucial in the modern digital age.
Read also: What is MIL-STD 810H: Standard Characteristics, Testing, and Usage
Advantages and disadvantages of end-to-end encryption
Despite being a powerful tool for protecting digital communications, end-to-end encryption (E2EE) has its strengths and weaknesses. Understanding these aspects can help individuals and organizations make informed decisions about using this encryption method.
Advantages of using E2EE

End-to-end encryption offers several significant advantages that make it a powerful tool for data security, protecting against invasive threats, and helping ensure compliance with regulatory standards. Some of the key benefits include:
- Protection against data transmission compromise, server breaches, and data center infiltration is one of the most critical benefits of end-to-end encryption (E2EE). We all know that the most devastating cyberattacks occur when a server is breached. In such cases, attackers can gain access to all the information stored on that server, compromising entire organizations or multiple entities with just one attack. With E2EE, data is encrypted the moment it leaves the sender’s device and remains encrypted until it reaches the recipient. This means that even if an attacker intercepts the internet traffic or breaches a cloud server or data center, they will only see scrambled, unreadable data. Thus, end-to-end encryption offers robust protection against some of the most severe data privacy breaches.

- Data leak protection is another key advantage of end-to-end encryption (E2EE). By keeping data encrypted and unreadable throughout transmission, the risk of data leakage is significantly minimized. In addition to encrypting data, most E2EE systems also use cryptographic methods to “sign” documents, ensuring their integrity. This “signature” is a set of numbers that verifies the sender’s identity, as only the sender holds the private key needed to generate the signature. Moreover, the signature includes the result of a mathematical calculation based on the document’s content. If even a single character in the document is altered, the calculation changes, alerting the recipient that the data has been tampered with. This gives the recipient confidence that the data has not been altered since it was created by the sender.
- Strengthening user trust. Thus, end-to-end encryption is crucial in sectors such as finance and healthcare, where protecting customer privacy is paramount, thereby increasing user trust in digital platforms.
- Compliance with data protection requirements is another significant advantage of end-to-end encryption (E2EE). Many industries face increasing cybersecurity compliance demands to address growing threats. E2EE can assist organizations in meeting strict data protection regulations, such as the General Data Protection Regulation (GDPR), which mandates strong measures to safeguard personal data. By ensuring that data is encrypted and protected throughout its transmission, organizations can more easily comply with these regulations and demonstrate that they are taking necessary steps to secure sensitive information.
Disadvantages
While end-to-end encryption (E2EE) is considered one of the safest methods for protecting data, no technology can guarantee 100% protection against all threats. Let’s examine some of the challenges associated with E2EE:
- Complexity in Implementation and Management: Setting up and managing end-to-end encryption systems can be technically challenging, requiring expertise in cryptography and secure communication.
- Difficulties in Data Recovery: If encryption keys are lost, the data may become irretrievable, leading to the potential loss of critical information. Once transmitted, recovering the information is practically impossible, which can result in the loss of confidential data.
- Potential for Abuse: While end-to-end encryption protects privacy, it can also be misused for malicious purposes, as it makes it difficult for authorities to access communications, even with a legal warrant. With E2EE, all data on the server is encrypted, meaning the service provider has no means to decrypt the data.
- Compliance Issues: In certain scenarios, end-to-end encryption can create challenges in meeting law enforcement requests, leading to potential conflicts with legal obligations. Authorities may have to resort to methods used for physical objects, compelling data holders to provide the information.
End-to-end encryption offers significant advantages in securing digital communication and protecting privacy. However, its implementation and management require careful consideration of potential challenges and drawbacks.
Read also: Best AI Music Generators That Are Already Available
The future of end-to-end encryption
The landscape of digital security is constantly evolving, along with the role and capabilities of end-to-end encryption.
Ongoing advancements in cryptographic methods, including algorithms resistant to quantum computer attacks, can significantly enhance the security provided by end-to-end encryption. These developments may necessitate updates and changes to current E2EE protocols to maintain their effectiveness against future threats.
Changes in data protection laws worldwide can impact the implementation of this encryption method, particularly regarding access to user data and cooperation with law enforcement agencies.

The future of end-to-end encryption is poised for significant evolution, both in terms of technological advancements and in response to changing regulatory landscapes. As E2EE becomes increasingly integrated into our digital lives, understanding its capabilities, limitations, and the importance of proper implementation will be crucial. Staying ahead of these changes and challenges will ensure that end-to-end encryption continues to serve as a cornerstone of digital privacy and security.
The importance of end-to-end encryption lies in its ability to provide secure communication between two parties while preventing any third party from accessing their conversation. This means that sensitive information, such as passwords, financial details, or confidential personal information, can remain safe during transmission.

End-to-end encryption remains a key tool in the pursuit of digital security and privacy. Its role and importance will only grow as we move into an increasingly connected digital world. Understanding the nuances, strengths, and limitations of E2EE is crucial for individuals and organizations to harness its benefits while being aware of potential challenges. As we move forward, the drive to develop and innovate this encryption method will play a critical role in shaping a secure and private digital future.
Read also:
- Qualcomm Snapdragon X Elite for Laptops: Everything You Need to Know
- What is Spatial Audio, How Does It Work, and How to Use It

