© ROOT-NATION.com - Use of content is permitted with a backlink.
Hacking has become an integral part of the Internet age. The whole world often talks about such events. We will also talk about it today.
The world depends on modern technology, and without it, it would often be impossible for government institutions, infrastructure, companies and ordinary people to function. This dependence also has an inherent negative side – cybercriminals who constantly expose us all to hacker attacks. Unfortunately, these attacks are often quite effective, leading to the theft of personal data, state and corporate secrets, and are used for malicious purposes such as espionage, blackmail, raiding, extortion, etc.

There have been many successful hacker attacks in the history of computer networks and the Internet. Cybercriminals have targeted a wide variety of targets, ranging from government and financial institutions to pipeline operators, industrial enterprises, energy facilities, etc. Sometimes, the damage caused by hackers led to a real collapse in certain industries, such as energy, transport and others, and required a huge amount of human and financial resources to overcome the consequences. We have selected a few examples of such hacker attacks and, unfortunately, we have to state that the level of electronic security in the world has not improved at all in recent years.
Let’s take a look at some of the most famous hacks that have gone down in history.
Yahoo leak (2013-2014)
In 2016, Yahoo reported a data breach following hacker attacks in 2013 and 2014, which had the effect of a real bomb blast. As a result of the hackers’ activities, information about the personal data of more than 1 billion people who used the platform’s services was freely available online. However, cybersecurity experts were confident that the actual number of victims was three times higher. And that was exactly the case. A year later, the American company was forced to admit it. The global community was shocked and very scared. The company’s shares plummeted, and users began to abandon Yahoo services en masse.

The news that the attack was carried out by the intelligence services of one of the countries added fuel to the fire. It became known that the perpetrators were hackers linked to Russian agents.
Hacking the PlayStation Network (2011)
The hacker attack on the PlayStation Network digital media and entertainment service in 2011 went down in history due to the enormous scale of negligence on the part of the company’s security specialists. The hackers stole data from about 77 million accounts and caused a real paralysis of the entire network. Worst of all, the intercepted information contained valid credit card numbers of the service users.

The employees of the Japanese company Sony, which owned this digital media and entertainment service, were in real despair, they did not understand what to do next. So they simply shut down their service for 23 days, allegedly trying to wait out the hacker attack. But the strangest thing was that no one started working on additional personal data protection. Users were furious, demanding that Sony take some decisive action. The hacker attack and the negligence of the company’s staff cost the company approximately $171 million. The popularity of the PlayStation Network digital media and entertainment service plummeted.
Something had to be done to prevent an even greater outflow of users. As compensation, PlayStation Network users received a month’s access to PlayStation Plus. In addition, Sony introduced identity theft insurance and provided funds as part of a settlement with people who were planning to sue the company.
Read also: The creation of AI: Who is leading the race?
OneCoin scam (2016)
This is no ordinary hacker attack, but a gigantic scam that for many years remained the largest cryptocurrency market scam in history. Only recently has the OneCoin case faded amid the bankruptcy of the FTX cryptocurrency exchange. This scam was a typical Ponzi scheme, i.e. a pyramid scheme created by the Bulgarian company OneCoin Ltd. Its founder was a Bulgarian woman, Ruzha Ignatova, who modestly called herself the “crypto queen”. She was assisted by another fraudster, Sebastian Greenwood.

They created a fake OneCoin token that could be bought and sold only on an internal exchange created by its authors. OneCoin Ltd claimed that OneCoin would be the “Bitcoin killer”. However, in fact, OneCoin coins were completely useless pieces of metal. At some point, the exchanger closed down “due to repair work”, and the funds were transferred to offshore accounts. By March 2016, more than $4 billion had been invested in the token on a non-existent blockchain. Thus, all the users’ funds were simply stolen and, unfortunately, were irretrievably lost.
Sebastian Greenwood was arrested in 2018 in Thailand, and his accomplice, Ruzha Ignatova, was on the run for a long time. But eventually she was arrested and extradited to the United States. She faces 40 years in prison. The lawsuits are still ongoing, and the fraudsters seem to have been arrested, but there is no money.
Read also: 7 coolest ways to use ChatGPT
Hacker attack on the Ministry of Defence and NASA (1999)
This is not only one of the oldest attacks on this list, but also one of the most interesting. In 1999, a 16-year-old hacker named cOmrade gained access to a computer network used by the US Defense Threat Reduction Agency (DTRA). His backdoors allowed him to download more than 3,000 messages. This allowed the young hacker to capture the login details of at least 19 employees. He was able to read secret documents and internal correspondence of agents without anyone suspecting it. Interestingly, the young man managed to hack into the router by logging in to the router. He managed to get the password from the router and seize the mailboxes of DTRA employees.

During the same period, the same hacker found a way to connect to 13 NASA computers at the Marshall Space Flight Centre in Huntsville, Alabama. This allowed him to download documents and software for managing the physical environment of the International Space Station. It is known that the cost of this software was estimated at $1.7 million at the time. It was very important for the ISS mission, as it maintained the space station’s environment, including temperature and humidity. After the incident, NASA had to suspend all operations for 21 days to determine the extent of the attack, spending $41,000 on contractor work and replacing the equipment.
This 16-year-old hacker became the first young hacker to be imprisoned for computer crime.
Read also: Russian hackers are trying to use ChatGPT for cybercrimes
Petya virus (2017)
On 27 June 2017, a powerful computer virus paralysed a number of companies around the world. The global outage was caused by the Petya.A ransomware virus, which blocks the operation of computers. The whole world then learned about the malware from the Russian hacker group Sandworm.
I’m sure many of you remember that hacker attack. The Petya.A virus encrypted information on a computer and then displayed a message demanding $300 in bitcoins to unlock it. Experts said at the time that the virus only affected Windows computers. Computers are infected through phishing emails (phishing is a type of online fraud where criminals gain access to confidential user data under the guise of emails on behalf of popular brands). Experts found out that the virus used a fake Microsoft electronic signature.
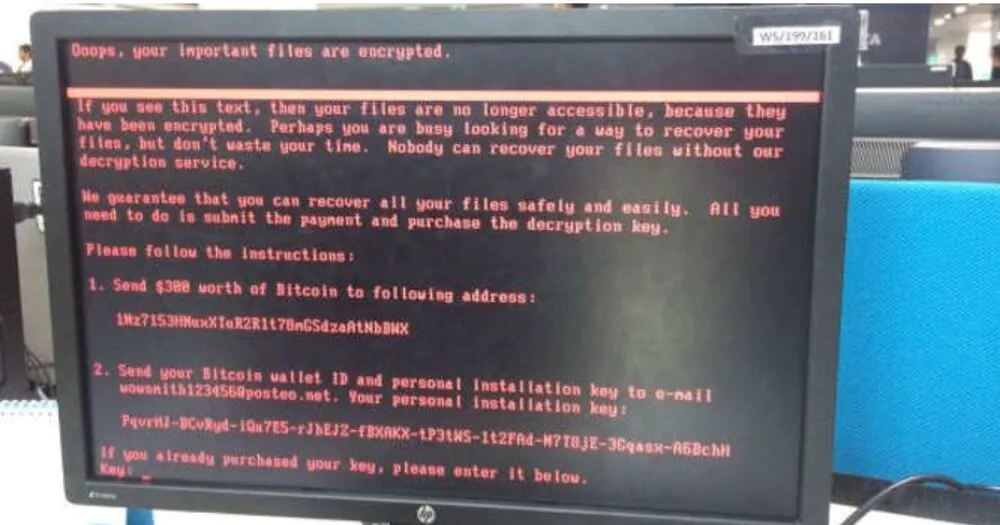
The Petya wiper (a data destruction malware that resembles ransomware) developed by hackers was distributed to computers of Ukrainian companies and government organisations, thus paralysing their work. Due to its properties, the software also began to spread elsewhere, including Europe and the United States. According to White House estimates, the cost of damage caused by the virus in the US alone exceeded $10 billion. The Ukrainian economy also suffered losses of $4 billion, and we felt the consequences for a long time.
Read also: ChatGPT: Simple instructions for use
Stuxnet (2010)
The Stuxnet worm is a versatile standalone industrial espionage tool designed to gain access to the operating system responsible for processing, data collection and operational dispatch control of industrial facilities. But unlike most similar viruses, Stuxnet’s main use may not be data theft, but damage to industrial automated systems. Worms of this class can stay in the system in a sleep mode unnoticed, and at a certain time start issuing commands that can disable industrial equipment.

This computer virus massively infected Windows computers in 2010. For a long time, cybersecurity experts have been trying to find a way to combat it. What’s more, it still exists today.
Stuxnet is known for being the first to be used to spy on and reprogram industrial plants. The software was created jointly by US and Israeli agencies, which used it to attack Iranian uranium enrichment facilities. By infecting Siemens Step7 control software, Stuxnet was able to damage centrifuges and disrupt the entire industrial process.
Read also: Ways Bitcoin is Recuperating the Planet
Uber data leak (2016)
In 2016, hackers launched a massive attack on Uber’s servers. Initially, it was said that the attackers stole the data of 57 million platform users and drivers. Interestingly, the case became public only in 2022, which caused a huge wave of criticism. At the same time, it became known that hackers managed to steal the personal data of as many as 77 million users and drivers.

The attackers managed to gain access to Teqtivity’s AWS backup server, which stored data on companies that cooperate with Teqtivity. In other words, the hackers got hold of information about users’ devices – serial number, brand, model, specifications, as well as information about the users themselves – name, surname, work email address, and information about their place of work. This has caused a great deal of international outcry.
Uber representatives also admitted that they had agreed to pay the hackers a $100,000 ransom to remove the ransomware, which is why the case was not made public in 2016. But the credibility of the Uber service was shaken.
Attack on the Marriott hotel chain (2014)
In 2014, hackers breached the servers of the Marriott hotel chain, stealing the credit card information of seven million British customers. To make matters worse, they were able to decrypt the data because the decryption keys were stored on the same server, including the customers’ passport numbers. A similar problem also occurred in 2016 at Starwood Hotels, which was acquired by Marriott. The worst part, however, is that the news of the information leak only came out in 2018, so for four years, hotel customers risked losing their money.

For a long time, the owners of the hotel chain simply did not want to make this hacking attack public. More than five million lawsuits were filed and are still pending. Although some customers have already managed to receive various amounts of compensation.
Read also: Blockchains of Tomorrow — Challenges and Solutions
Attack on Kasey’s global customer base
Hackers from REvil prepared a ransomware that, after gaining access to the servers of the SolarWinds management service provider, spread to Kasey’s global customer base. The malware was distributed to 60 companies that work with Kaseya via a fake update to the VSA servers used for remote monitoring and management.
This sophisticated attack, which occurred in 2021 just before the US Independence Day celebrations, affected hundreds of US companies that used the services of Kaseya, a software company that provides software and services for many companies’ internal computer networks.
The exact number of victims of the attack is still being determined, but it is already known that, in addition to American companies, other firms and organisations have been affected, including 600 Swedish Coop supermarkets, two Dutch IT companies, and even 11 schools in New Zealand.
Kaseya itself claims that less than 40 of its customers were affected. But since Kaseya provides software to companies that in turn provide IT services to many other companies, the number of victims could be much higher.
Read also: Exploring Oracle HCM Cloud Features: What You Need to Know
Hackers against the Colonial Pipeline
This is one of the most recent examples on our list, and at the same time the largest attack on infrastructure in the United States. Russian hackers from the DarkSide group infected the system of Colonial Pipeline, which operates an oil pipeline in the southeastern United States, with ransomware.
Colonial Pipeline fell victim to a ransomware attack in May 2021. As a result, some of the pipeline’s digital systems were infected, shutting it down for several days.

The outage affected consumers and airlines along the east coast. The hack was deemed a national security threat as the pipeline transports oil from refineries to industrial markets. President Joe Biden even declared a state of emergency because of this.
The attack led to the temporary closure of many petrol stations, particularly in Virginia. DarkSide demanded a ransom of about $4.4 million. Colonial Pipeline paid the DarkSide hackers to obtain a decryption key, which allowed the company’s IT staff to regain control of its systems. However, most of the ransom was later recovered by US intelligence agencies.
The Role of Cybersecurity Experts and Solutions
Cybersecurity experts play a vital role in protecting systems and networks by conducting audits to assess security measures, identifying areas for improvement, and testing systems for vulnerabilities. They review access controls, ensure compliance with industry standards, and actively monitor networks and systems using intrusion detection systems, log analysis tools, and threat intelligence feeds. By participating in cybersecurity communities and collaborating with other experts, they stay updated on emerging threats, trends, and countermeasures.
Enterprises must evaluate the security practices of third-party vendors and suppliers, conducting security assessments, due diligence, and establishing contractual requirements. Additionally, implementing continuous monitoring systems such as Security Operations Centers (SOCs) with Security Information and Event Management (SIEM) tools, threat intelligence feeds, and advanced analytics helps respond to security incidents in real-time. To defend against corporate account takeover (CATO), where attackers gain access to business email accounts to initiate fraudulent transfers, enhanced email security and employee education are critical.
To safeguard against cyberattacks, a combination of technical solutions, employee education, and proactive security measures, such as enabling two-factor authentication, is crucial. Cybersecurity is a shared responsibility, and enterprises must prioritize these measures.
The financial losses, operational disruptions, reputational damage, and national security implications highlight the urgent need for organizations to prioritize cybersecurity. By implementing proactive measures, raising awareness, and collaborating with experts, organizations can enhance their resilience and mitigate the risks associated with cyber threats.
The world around us, the Internet and ourselves are constantly changing. We live, communicate, work, and improve ourselves in a whirlwind of events and information. Of course, hackers are not resting on their laurels either, trying to constantly improve their skills and means of hacking and DDoS attacks. Therefore, you should remember that it is up to you to keep the Internet safe. Be careful and take care of yourself!
Read also:

