© ROOT-NATION.com - Use of content is permitted with a backlink.
Two-factor authentication is a secondary verification of identity when you log in to the service or the website. But why is it recommended to use it? What is the use of it?
Almost everyone knows or at least has heard about two-step verification (two-factor authentication, also called Lockdown, and not related to COVID). It is most often used, for example, in financial applications that use this method of authorization to improve the security of operations.
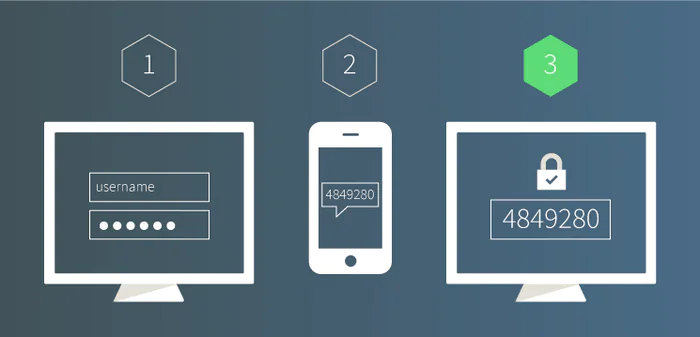
It’s time to learn some important information about two-step verification. Until passwordless login mechanisms are improved, this is the best way to protect our accounts from being hacked.
What’s Wrong With a Regular Password?
We answer! As you know, many people ignore any security rules and use easy-to-remember passwords like 12345, 11111, qwerty123 (it’s even more “complicated” than just qwerty), and so on. And even if you force people to create passwords with special requirements, they will suffer in every way to avoid it (after all, not everyone wants to use password managers).
Avoid and … come up with tricks — add some number like “1” or an exclamation mark to a complex password and use it everywhere. As a result, if Internet attackers receive your data for logging into one website, they will try to check all other possible sites and services. What if they are “lucky” and the password opens the door in another place?
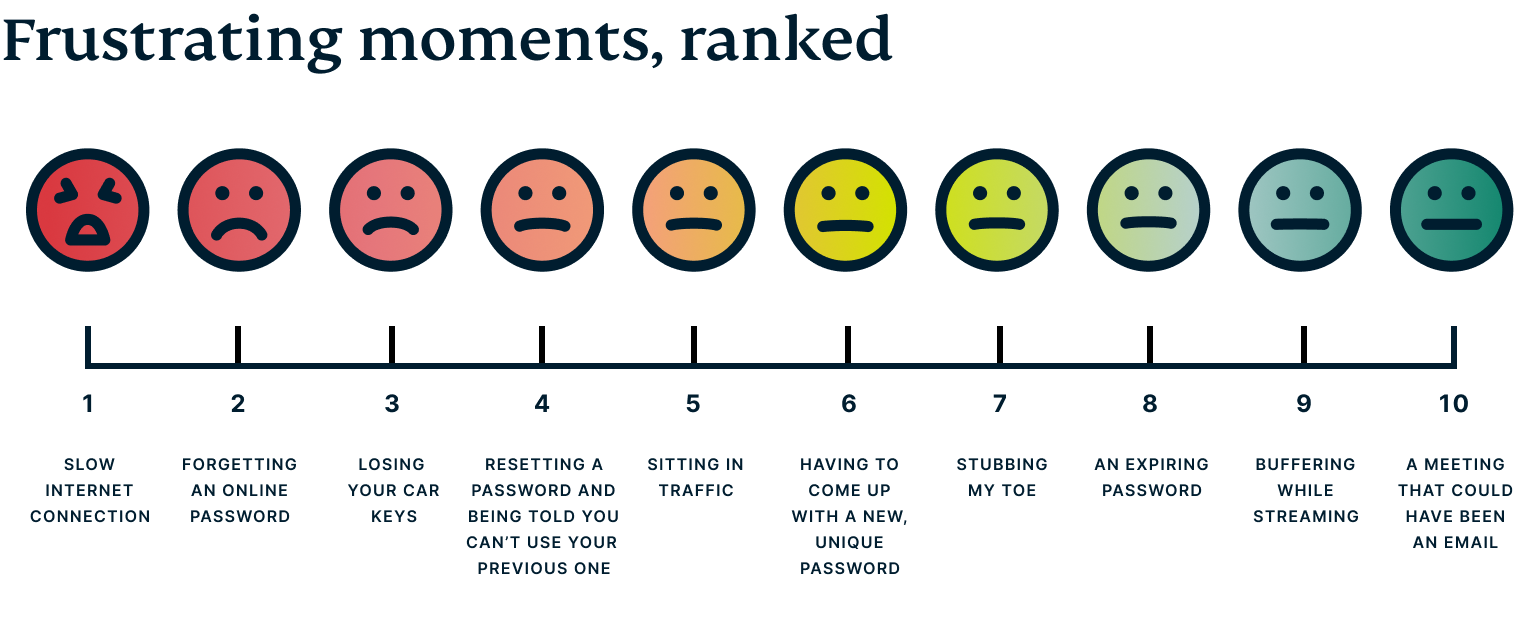
Online banks have high requirements for passwords. What does this lead to? To people forgetting their passwords and resetting them regularly. According to research conducted by ExpressVPN, up to 20% of respondents in different countries use the password recovery option at least once a month! And 76% of those surveyed were “thrown out” of their account at least once after entering the wrong password several times.
Research says that having to reset your password ranks second on the list of annoying things! Above is only a slow internet connection. Less annoying events are loss of car keys, standing in traffic, interrupted audio, etc.
What we can learn from this is that people need an additional level of protection in addition to a password. And this is exactly what the famous two-factor authentication helps with. Let’s get to know it better.
How Does Two-Step Verification / Two-Factor Authentication Work?
When you log into your account, you must not only specify the correct password but also enter an additional code generated earlier or sent to your device. This level of security ensures that even if someone gets the password to your account, they won’t be able to access your profile without entering an additional code.

Two-factor authentication also has additional advantages. In the case of an unauthorized request to enter the account, you will receive a notification, and you will be able to change the password immediately so that in the future you do not have to worry about the fact that someone got hold of your personal data. In addition, this method allows you to protect yourself even in the event of a mass leakage of passwords when a service is hacked. Criminals will not be able to bypass two-factor authentication.
What Can I Use for Two-Step Verification?
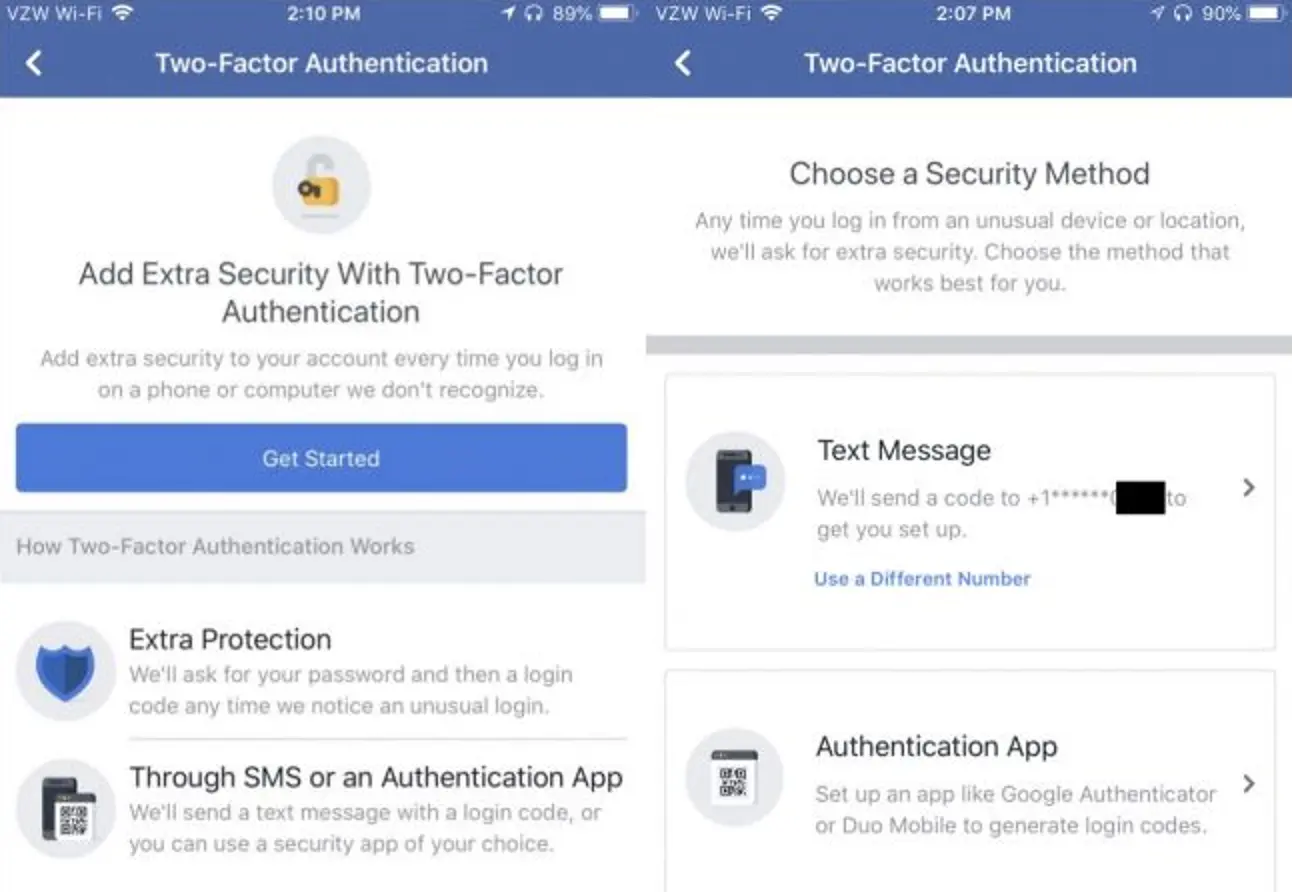
For two-factor authentication, you can use:
- code received by e-mail;
- phone call with confirmation;
- smartphone or phone – code sent via SMS;
- smartphone or tablet – key generation apps, such as Google Authenticator and Microsoft Authenticator, or other mobile authorization applications, such as banking client applications;
- OTP tokens (one-time codes);
- a physical security key (U2F security key) connected to the USB port (for example, a Yubico or HyperFIDO security key).

Now I Have To Enter Two Passwords Each Time?
No, you don’t need to do this every time. You need to understand that after logging into a computer, you can add it to the list of trusted devices (for example, if it is a home computer). This way, after a successful two-step verification, you will be able to log in, as usual, using your password.
But Why Do I Need This if I Do Not Store Important Data in the Mail or in the Cloud?
You need to be aware of the risks associated with hacking your email account, network drives, Google services, or social networks such as Facebook, Instagram, Twitter, and others.
Let’s be honest. Have you ever uploaded electronic documents or a screenshot of important correspondence, tax returns, or even a copy of your passport or ID card to cloud services? If the answer is no, then the data that the web services contain is enough to steal your digital identity and use it for personal gain.
The data you once emailed may still be in your Inbox or Sent Items. The thief can even use the data to take out a loan using your passport details. And this is just the tip of the iceberg, which can lead to many unpleasant and often costly situations. Email hacking is not a trivial matter and cannot be underestimated.

People who conduct their business using the tools provided by Google, Microsoft, or Facebook face another problem: the loss of access to an account and the leakage of personal data can be tragic events for the company. This is already far worse in terms of financial consequences than the loss of private personal data.
Losing your Steam, Origin, and Epic accounts (which recently started requiring two-step sign-in for free games), your ISP or mobile operator account can also backfire and be a significant loss for many users.
How to activate two-factor authentication?
All you need to do is enable the two-factor authentication feature in the settings of a specific application, site, or web service.
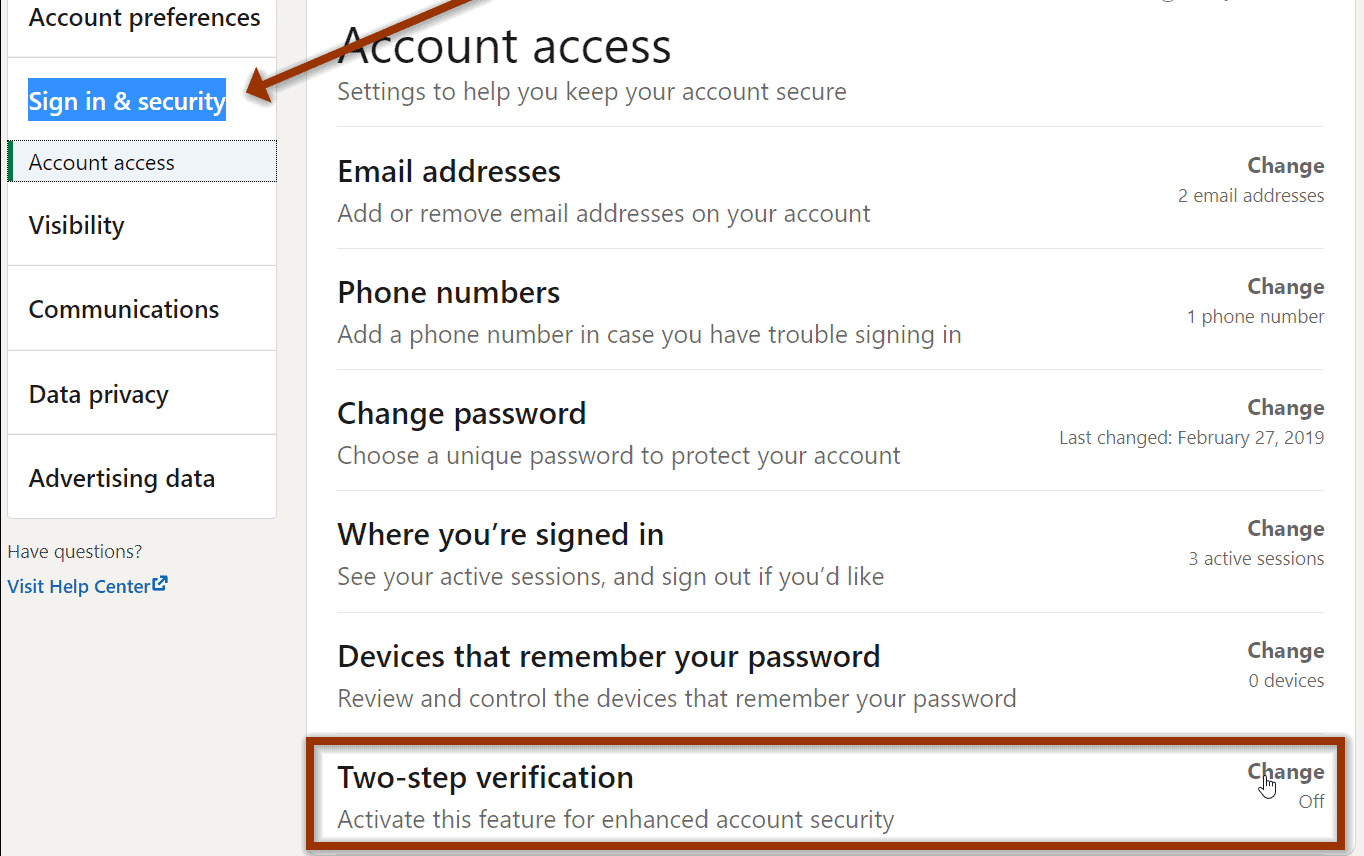
The system itself will offer to perform the necessary actions and issue backup codes to access the account if necessary. Save them in a safe place, preferably in physical form (print or save to a file on external media).

If the service provides for two-step verification, there will definitely be options for sending SMS codes to a phone number or confirmation by an application (or a code generator). Some services also allow two-step verification using a physical FIDO U2F key.
When I Set Up My Account, I Provided a Phone Number for Password Recovery, Is This Two-Factor Authentication?
Unfortunately, no. With the ability to recover your password by adding your phone number, you will be able to recover an account (that someone has hacked and changed your password). But it won’t help you avoid a data breach.
Should I Use This Method of Identification, or Is It Better To Switch to the Increasingly Popular Passwordless Login?
By passwordless login, we mean, for example, logging in using biometric data, such as Windows Hello or FIDO2-compliant physical keys. Physical FIDO2 keys are certainly worth considering, but we wouldn’t use biometric-only logins without additional security. Biometric data can also leak onto the Internet.
By far the simplest, most efficient, and cheapest method is the two-step verification. Even the simplest SMS protection gives you more security than logging in with just one password. Apps like Google Authenticator are more reliable and secure.
Well, for business users who have a lot of corporate secrets, it is best to use U2F physical keys. But be prepared for the fact that although they are inexpensive, you will need to carry them with you all the time (usually the keys exist in the form of small USB flash drives). But such security keys will provide more reliable protection than ordinary passwords.
Will I Feel Completely Safe With 2-Step Sign-In?
This method will greatly increase your security, but not all of its options can be considered 100% safe. Two-step sign-in is just one of the many digital security challenges that also include network traffic encryption and tracking protection (VPN), data carrier encryption, or simply understanding threats like phishing.

Of course, when using two-factor authentication, you should not forget that you must also be vigilant and attentive on the Web, use complex passwords, and not download or open unknown files and attachments. Remember that attackers try to make the most of human weaknesses. Using two-factor authentication will help protect personal data, trade secrets, and money as much as possible.
Recommended article: Top Tools to Use besides a Firewall to Protect your Network

