© ROOT-NATION.com - Use of content is permitted with a backlink.
When it came time to make a video about the Wings and Jeweller technologies from the Ukrainian security systems manufacturer Ajax Systems, I essentially had no choice but to start with… Diablo. Yes, the first one. Because Diablo from 1997 became for Blizzard what a pair of wireless standards became for Ajax: something monumental, significant for the history as a whole, and… unexpected for everyone.
Video review of Wings and Jeweller by Ajax

A bit of history
Few people remember, but Blizzard, or Activision Blizzard, was originally called Silicon & Synapse and developed several games, including the quite good platformer *Lost Vikings*. However, this was not the classic Blizzard we know today.

Until it released Diablo. It wasn’t the first game Blizzard released after changing its name, but Diablo cemented the company’s position and marked the beginning of its golden age.

So, there are two versions of the story. The first was shared by David Brevik, co-founder of Blizzard North and game designer of the series, at GDC 2016. He mentioned that the idea had been with him since almost college and that the pitch for the game began long before Blizzard Entertainment was created. It only came to fruition after the release of Warcraft, and it was Blizzard South that suggested making the game in real-time, which Brevik was initially against…
But there’s a second version. It doesn’t entirely contradict the first, so I’m inclined to stick with it. However, I haven’t found confirmation for this version, so I can’t position it as the definitive account. So, here it is… Diablo didn’t originate from the idea of creating a role-playing game about a terrifying dungeon, or from the story of the actual Lord of Terror, Diablo.

The game was born… from the interface. As far as I know, a graphic designer was experimenting with interfaces and came up with a very stylish one. Life on the left, mana on the right, gothic icons, dark fantasy. It turned out to be very, very cool.

Inspired by this interface, the game designers began to develop the idea further. Certain pillars and foundations of the game took shape: brutal fantasy, some of the most terrifying and brutal cutscenes, and a heroic storyline involving self-sacrifice. Add to this the idea of creating a real-time role-playing game instead of the turn-based ones that were common at the time, and you get the birth of the hack & slash genre.
Parallels
So, what does this have to do with Ajax? Because when the company first attempted to enter the international market, it already existed and had a product. That product was a failure—something even the company’s founder, Oleksandr Konotopskyi, admitted. It was the invention of Jeweller and then Wings that not only made up for the “sticky first pancake” but also transformed Ajax into what it is today: a global leader in home and business security with almost no competitors in the field.

And they are absent precisely because, until around 2012, the security industry lacked wireless communication protocols that were reliable enough to prevent attackers from quickly blocking, intercepting, or jamming them. And that was the case… until the emergence of Wings and Jeweller.
The moral of the story? It doesn’t matter when your company was founded. It doesn’t matter whether its first product was successful, or whether the second or third product was a hit. Success can come in completely unexpected ways—either by being inspired by something small amidst other things or by turning a failure into an opportunity and approaching the problem from a different angle.
Directly about the topic
However, I won’t be sharing much about the data transmission protocols, and for very simple reasons. This is also why I’ve shown very little about Ajax devices in my videos, for example. The less the public knows about what, where, and how protects your home, the better it is for you, as it makes it harder to, say, plan a burglary.

Ajax will never reveal ALL the details of the Wings and Jeweller standards while they are still in use. The reason, I think, is obvious. Additionally, you should know that Jeweller is a data transmission channel between devices and the hub. It is energy-efficient, has constant and rapid polling, and is protected against tampering and hacking. Nearly all other Ajax technologies are built on its foundation.

Wings is a similar protocol—so similar that even the manufacturer doesn’t describe it very accurately. The main page states that this protocol is “backup,” which isn’t quite right. It doesn’t act as a backup for Jeweller; rather, it operates independently, working alongside Jeweller, and is responsible for handling large data volumes. Initially, it was used for transmitting photos from sensors for photo verification. Over time, its functions expanded to include language settings, air quality sensor data, firmware updates, and more.
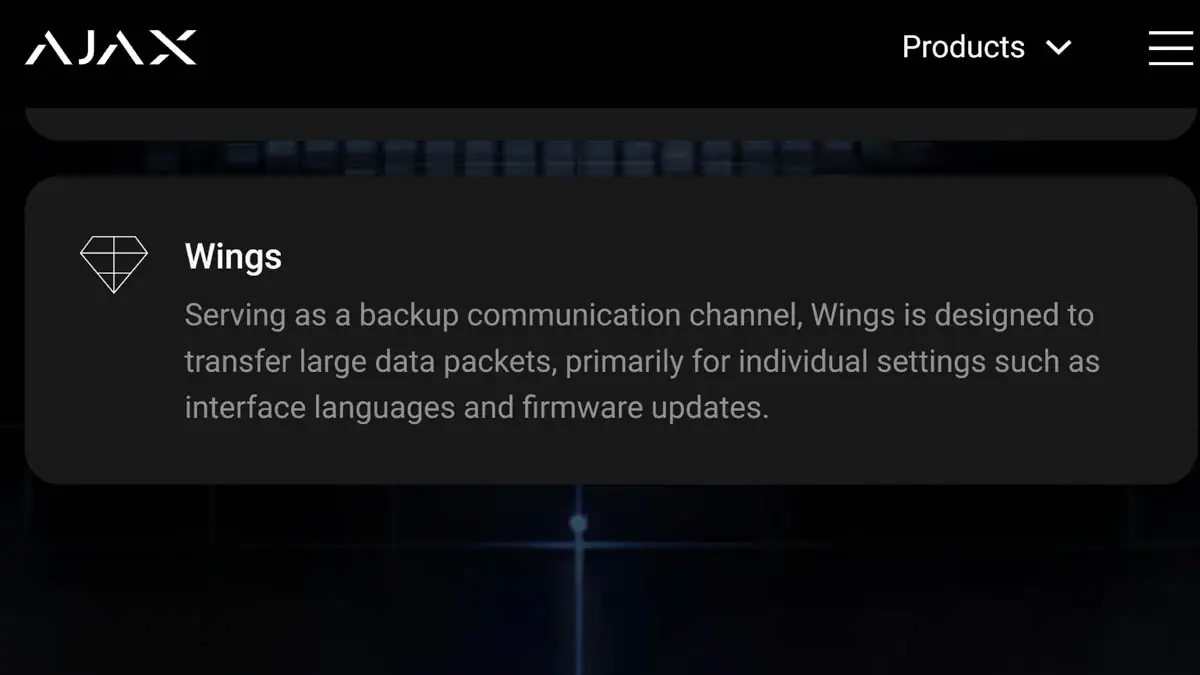
While Jeweller handles small data volumes with continuous and maximum speed transmission, Wings deals with large data packets with optimal energy efficiency. Think of the cache in a processor: L1 is fast but limited, while L3 is slower but larger. Jeweller and Wings serve different purposes and don’t overlap, and it’s important to understand that. It’s also crucial to know that to use these protocols, you must have an Ajax hub; just a smartphone won’t suffice.
The cost of technology
This, by the way, answers the question of why hubs are so expensive. They are relatively costly, even compared to other Ajax products. However, there is an important and key explanation for this cost. Each hub contains proprietary Ajax technologies, including those for Wings and Jeweller. The connection between, say, a “smart” socket from AliExpress for 150 UAH and a smartphone can be relatively easy to intercept (and that’s if the socket isn’t already sending your data to China from the start).
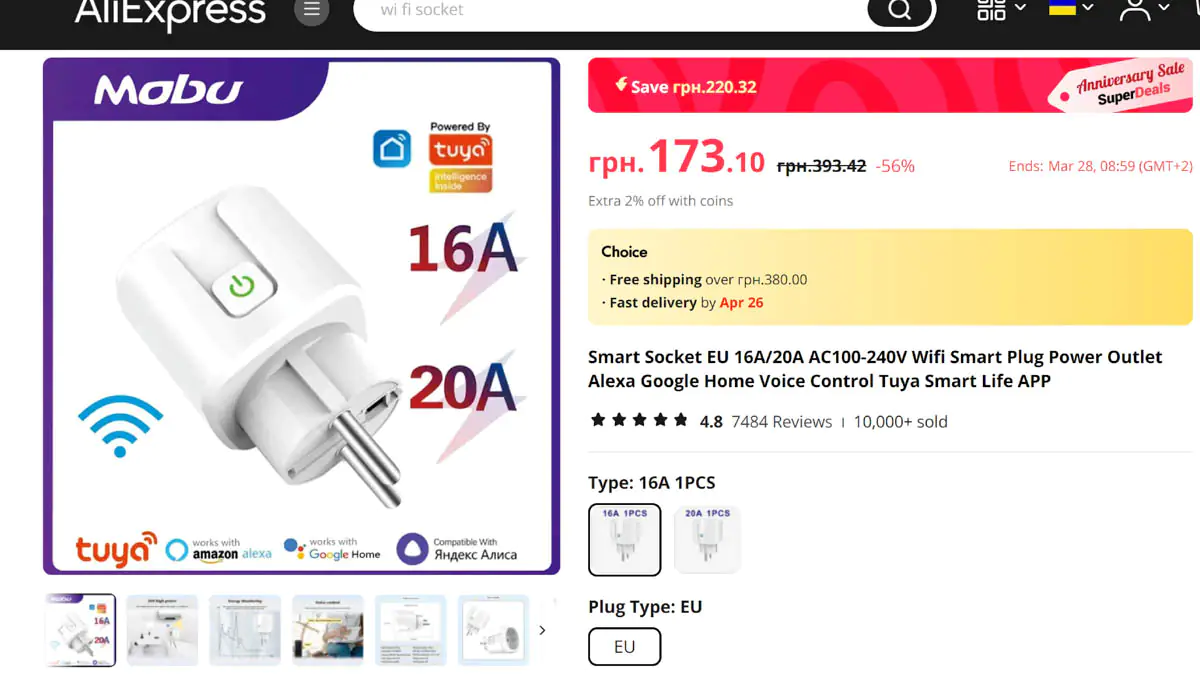
Data transmission between Ajax and a smartphone over Wi-Fi or the network can theoretically be intercepted. Similarly, it’s theoretically possible to hack Wings and Jeweller. However, while both are wireless communication standards, they are very different and transmit very different types of data. Hacking the protocol would require millions in equipment, exceptional skills, and sheer luck—much like bringing down the only F-117 in Serbia. You’d need to bypass proprietary markers, properties, counters, checksum verifications—but theoretically, it is possible.

With much higher likelihood, however, a criminal would try to gain access to your account. That’s why the system includes two-factor authentication, fingerprint verification, session controls, and more. So, with basic device security skills, you get a security system that’s nearly impossible to hack.

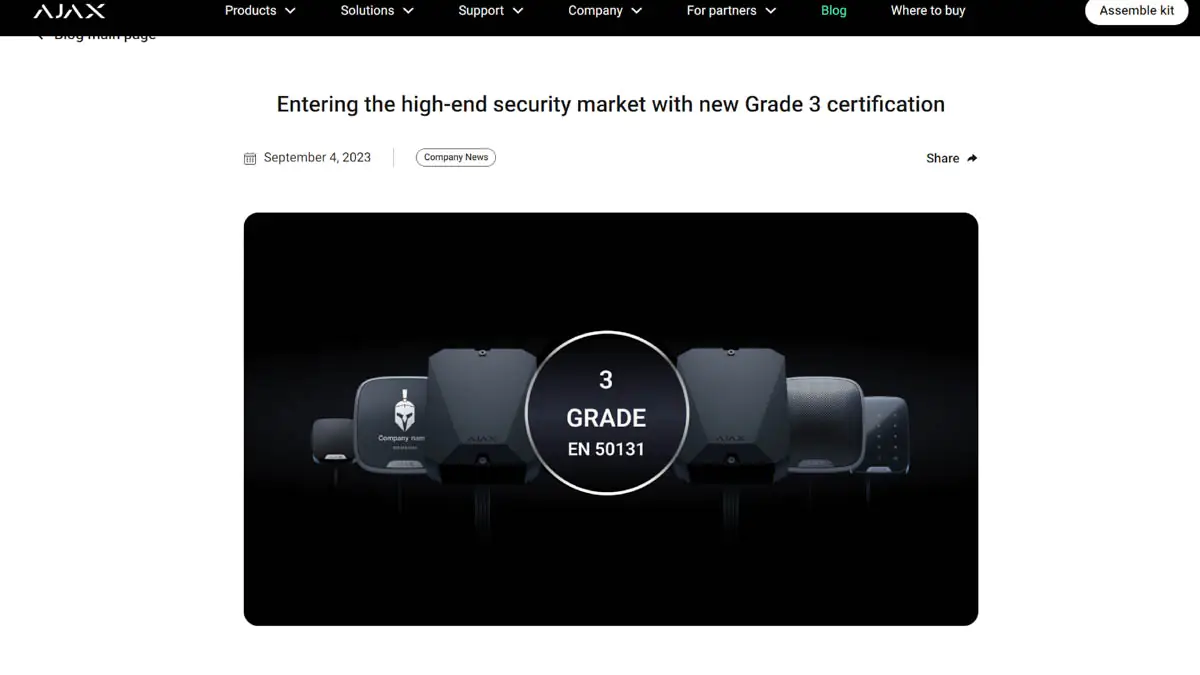
And that’s precisely why using Ajax security systems is recommended not just for large corporations with billion-dollar profits, but at least for home use as well. For larger firms, Ajax offers a separate line of wired models with a distinct and robust Grade 3 security class.
But that’s for large projects. For home use, a basic combo with an alarm system, a door camera, and a hub will cost around $300, but will require millions in equipment to crack. This will be beyond the reach of an ordinary thief and will make you less interesting to more serious individuals.
So, this combo, by the way, with the Ajax HomeSiren, the Ajax MotionCam motion sensor that captures photos during an alarm, and the Ajax Hub 2 4G central with cellular communication, is what I recommend for an apartment in a high-rise building. The siren is the last device that arrived in my complete set, and it’s extremely loud. So loud that the neighbors will hear it and come to check. Especially in buildings with poor sound insulation.
Summary
Security, affordability, and widespread use are all thanks to Jeweller and Wings. These two data transmission protocols have shaped Ajax into the company we know today, and the one known worldwide. Also, don’t worry, we regularly write about the company’s new products and do so with pleasure.
Read also:
- What Will Happen to Windows 10 After Support Ends
- Top 10 Most Interesting Modern Horror Films on Netflix
- What is MIL-STD 810H: Standard Characteristics, Testing, and Usage

